
Proxy servers are used by businesses and parents to oversee and supervise how their staff or children use the web. Most companies don’t want you to visit certain websites on business time, therefore they can set the proxy to block access to certain sites rather than diverting you with a kind message urging you to abstain from visiting those sites on business hours. Here are the different types of proxies that you can pick from according to your need.
Forward proxy
A forward proxy is a server that sits next to the client and distributes data to sets of people on an interior network. When a function is started, the proxy examines it to see if it should be accessed or not.
Internal networks that require an unique point of reference are best served by a forward proxy. It secures IP addresses for individuals on the system while also allowing for simple administrative administration. A forward proxy, on the other hand, may hinder an organization’s capacity to cater to the demands of certain end-users.
Transparent Proxy
A transparent proxy can provide users with the same feel as if they’re accessing their own pc. It is “transparent” in this sense, users can be “compelled” to join, which means they are linked without their knowledge.
Transparent proxies are ideal for firms that like to utilize a proxy but don’t want their workers to know about it. It offers the advantage of providing a unified user experience. Transparent proxies are more vulnerable to security risks such SYN-flood refusal assaults.
Anonymous Proxy
The goal of an anonymous proxy is to make online activity invisible. It operates by connecting to the web on the user’s pc while concealing the user’s identification and computer data. People who seek complete privacy when browsing the internet should utilize a transparent proxy. While transparent proxies offer a few of the greatest anonymity protection available, they do have significant disadvantages. Many people consider the use of transparent proxies to be unethical, and users may risk backlash or discrimination.
High Anonymity proxy
A high anonymity proxy is like an incognito proxy that goes a step farther in terms of anonymity. It operates by wiping your confidential info well before proxies connect to the destination site.
The server is especially suited for users that want complete anonymity, such as workers who don’t want the online activities to be traceable back to the company. On the flip side, a few of them, notably the free ones, are only decoys designed to entice users into disclosing personal data.
Secure sockets layer proxy
Among the user and the host, a secure sockets layer (SSL) proxy offers decryption. The proxy conceals its presence from simultaneously the user and the host since the information has been encrypted both ways. Thepirateproxybay.com is the great proxy server of SSL. You must try this if you wish to go with a secure sockets layer proxy server.
Such proxies are appropriate for businesses that want additional security against attacks that the SSL protocol detects and blocks. As Google likes SSL-enabled servers, using an SSL proxy in conjunction with a site may improve its search term position. On the disadvantage, material encrypted using an SSL proxy could be cached, thus you may notice poorer performance while accessing websites numerous times than you might normally.
Distorting Proxy
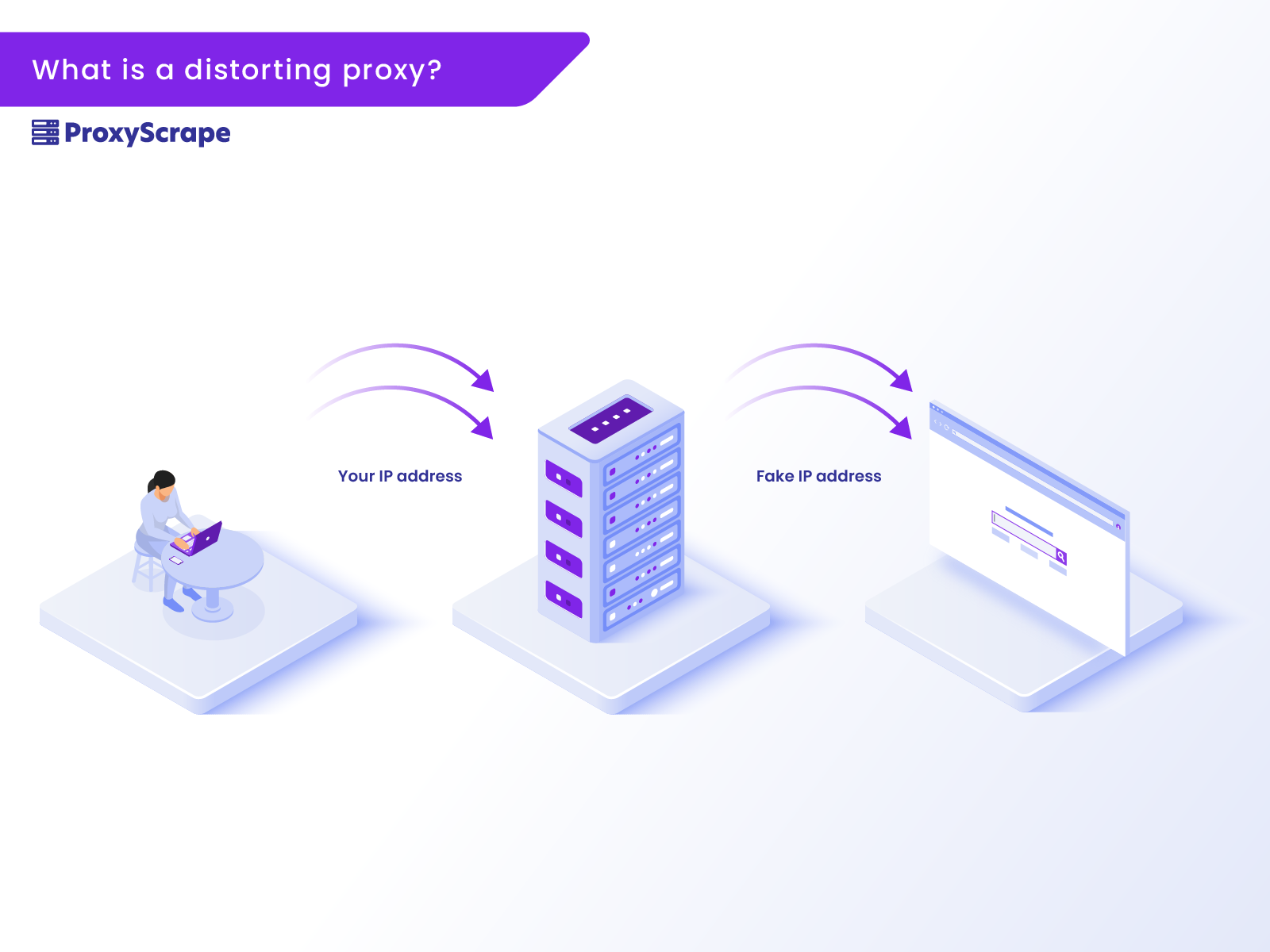
A distorting proxy reveals itself to a site as a proxy while concealing its true identity. It accomplishes this by altering its IP address to one that is wrong. Individuals who wanted to mask their address when surfing the internet should use distorting proxies. This form of proxy may make it appear as though you’re surfing from a certain nation and has the added benefit of concealing not only your identification but also the proxies. This implies that even if you are connected to the proxy, your information remains safe. Some websites automatically disable distorting proxies, preventing users from reaching the sites they require.
Datacenter proxies
Datacenter proxies are not tied to an ISP and are provided with another firm through a data center. The user’s queries are forwarded via the proxy server, which is located in an actual data center. People that want rapid reaction times and a low-cost solution might consider data center proxies.
As a result, they’re a wonderful alternative for anyone who needs to swiftly obtain information on an individual or organization. They have the advantage of allowing users to collect data quickly and cheaply. However, they do not provide the utmost level of anonymity, putting users’ information and identities in danger.
Residential proxy
A residential proxy assigns you an IP address associated with a portable computer. The gadget is then used to relay all queries. Residential proxies are ideal for people who need to double-check the advertising that appears on their site, allowing them to prevent cookies, dubious, or unwelcome adverts from rivals or unscrupulous actors. Other proxy alternatives are less reliable than residential proxies. However, because they are frequently more expensive to use, customers should seriously reconsider if the benefits outweigh the additional expense.
Public proxy
Anyone may use a public proxy, and it is completely free. It operates by offering people access to its IP address, which allows them to remain anonymous when visiting websites. Public proxies are suitable for those who are concerned about money rather than security or performance. Since they are simple and easy to use, they are frequently sluggish due to a large number of users. If you’re using a public proxy, you enhance the chances of your data being accessible by someone on the web.
Shared proxy
Shared proxies are being used by several users at the same time. Users are given a unique identification that differs from the address given to the device that connects before them.
Shared proxies are a good choice for individuals who don’t want to spend money and don’t require a good connection. A shared proxy’s key benefit is its cheap cost. Since they are distributed, you may be held responsible for others’ poor judgments, which might result in you being blacklisted from a website.
Rotating proxy
Every user that accesses a rotating proxy is assigned a distinct IP address. Users are assigned an identity that is distinct from the address assigned to the device that connects before them.
Users that need to perform a bunch of high, continual web scraping should employ rotating proxies. They enable you to visit the very same website repeatedly while remaining anonymous. When it comes to rotating proxies services, you must be cautious. Many of them use public network proxies, which might reveal your information.
Reverse proxy
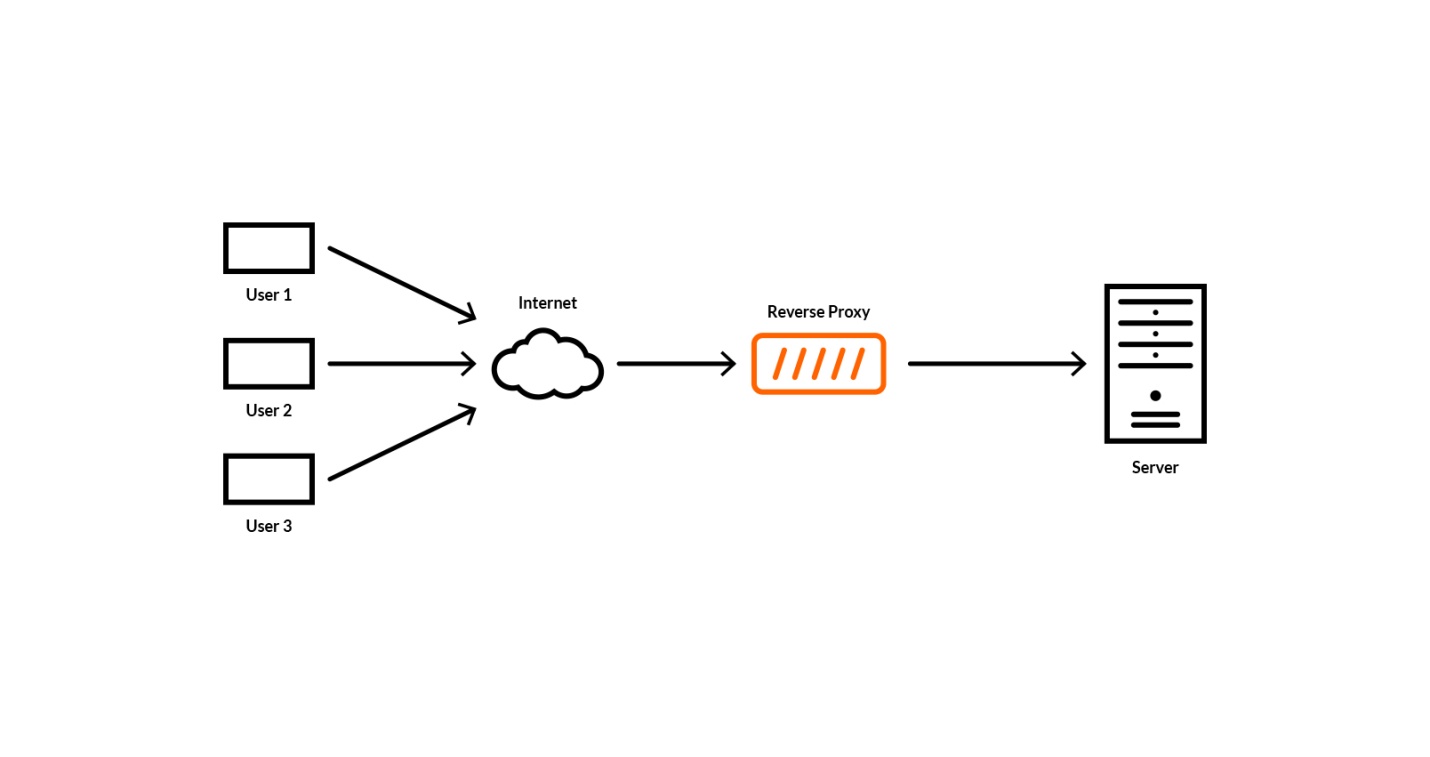
A reverse proxy, resembling a forward proxy, lies in front of servers and sends queries from browsers to the servers. It intercepts the user’s request at the server’s edge networks. The responses are subsequently sent to the origin server, which responds with responses. For popular sites which need to distribute the workload of a large number of received requests, reverse proxies are an excellent choice.
Since they manage requests like just another web server, they can assist businesses cut bandwidth use. On the other hand, if an intruder is able to bypass reverse proxies, they can reveal the HTTP server structure. If a reverse proxy is used, network managers will need to ramp up or relocate their firewall.
Conclusion
For the sake of personal security and network efficiency, contemporary proxy servers are becoming much more important nowadays. Proxy servers operate as a barrier and web blocker, as well as providing shared connectivity and caching data in order to speed up large numbers. Users and the internal network are safeguarded by a decent proxy server from the evil things that live out on the wild internet. Finally, pick your proxy servers from the above-mentioned list according to your need, so that it can provide you with a lot of privacy.
Leave a Reply